Computer Science
Formal evaluation of network security
- Verification of cryptographic protocols using formal methods -
Abstract
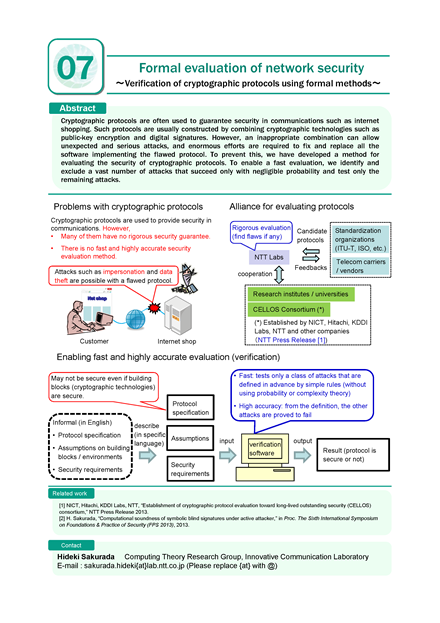
Cryptographic protocols are often used to guarantee security in communications such as internet shopping. Such protocols are usually constructed by combining cryptographic technologies such as public-key encryption and digital signatures. However, an inappropriate combination can allow unexpected and serious attacks, and enormous efforts are required to fix and replace all the software implementing the flawed protocol. To prevent this, we have developed a method for evaluating the security of cryptographic protocols. To enable a fast evaluation, we identify and exclude a vast number of attacks that succeed only with negligible probability and test only the remaining attacks.
Photos
Poster
Map
Presentor

Kunihiko Fujita
Innovative Communication Laboratory
Innovative Communication Laboratory

Yasuyuki Tsukada
Innovative Communication Laboratory
Innovative Communication Laboratory